October 2020, Vol. 247, No. 10
Features
Evolution of Effective Design for Alarm Management Applications
By Whitney Vandiver, Pipeline Compliance, NuGen Automation
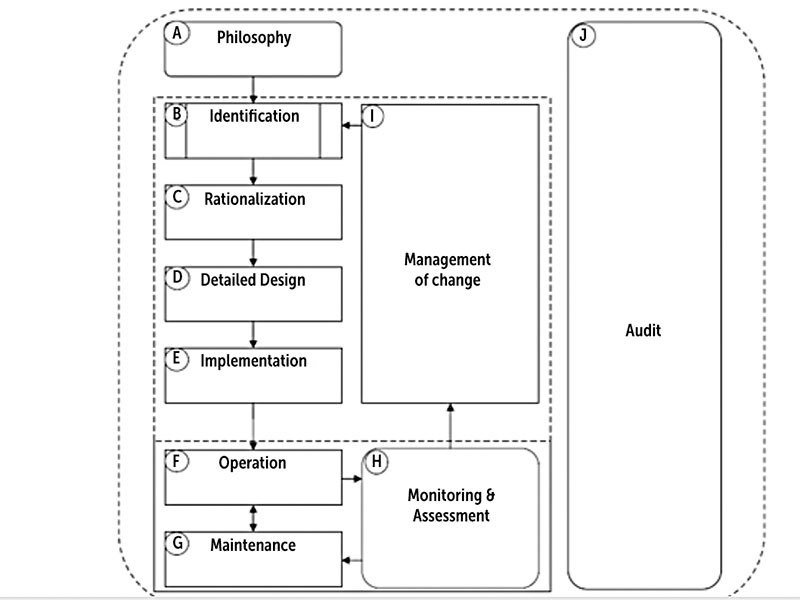
The regulated process of alarm management is captured in the lifecycle model outlined in ANSI/ISA 18.2 Management of Alarm Systems for the Process Industries.1 While each stage of the lifecycle is imperative to the complete management of alarms, one of the loops within the lifecycle is that of alarm management operation, maintenance and monitoring and assessment.
By recording that data during an alarm system’s operation, a user can monitor and assess alarm performance, informing the maintenance of the system along with producing recommendations for management of change. While the path between operation, maintenance and monitoring and assessment can be cyclical, it can also lead to improvements throughout the alarm management plan by introducing modifications that support the alarm philosophy but require all aspects of the lifecycle for completion.
Proper management of alarms throughout their lifecycle requires consistent monitoring and awareness of the causes of alarms as well as their behavior. The advent of advanced SCADA systems brought with it richer data that provided better insight into minute-to-minute operations as well as trends in alarm behavior, leading the oil and gas industry to seek innovative control room management solutions.
Specialized applications have become the norm for high-performance data analysis in today’s market, and these applications have continued to evolve as technology trends push big data analytics to the forefront of the automation industry.
Monitoring, Assessment
At their core, alarm management applications focus on the entirety of the alarm management lifecycle; however, once an alarm management plan is in place, the driving force behind its continued evaluation and improvement lies in the monitoring and assessment stage. The objectives of alarm monitoring and assessment are:1
- measuring quantitative facets of alarm system performance
- comparing quantitative and qualitative measurements against KPIs
- identifying problematic behaviors to drive alarm system improvements
Through the pursuance of these objectives, control room managers will gain insight into specific aspects of their alarm systems, such as an understanding of sources of alarm behavior, identification of legitimate alarms and determination of the cause of problematic behavior such as nuisance alarms and alarm floods. As a standard practice in control room management, alarm monitoring and assessment begins with the collection of alarm data via the SCADA system, benchmarking for a baseline comparison, analysis of relevant data and the implementation of management techniques unique to a given system.
Alarm Rationalization
As an early stage of the lifecycle, alarm rationalization must occur for proper management of alarms to follow; however, as with monitoring and assessment, it is revisited if alarm performance proves inadequate and requires changes to be made in the rationalization of alarms.
Because each stage of the lifecycle feeds into the next, alarm rationalization continuously affects the performance of an alarm system and thereby the results of alarm monitoring and assessment. It is during alarm rationalization that criteria for alarm configuration is applied to individual alarms, and this underlying structure informs the data recorded in SCADA historians for monitoring and assessment. Conversely, the techniques used in monitoring and assessment can affect the impact that the stage has on proving that alarm rationalization has been achieved.
The alarm management process is most readily regulated by ANSI/ISA 18.2 and API 1167 Pipeline SCADA Alarm Management, which require that regular monitoring be performed to assist with the maintenance of an effective alarm system while frequent assessment evaluates many aspects of alarm behavior.2
Given the amount of data that can be pulled from a modern SCADA system, complying with regulating agencies’ requirements for continued alarm monitoring and assessment is no small task. As the demand for a solution to big data analysis developed, so did advanced applications that aim to present valuable data in a functional and flexible platform.
Comprehensive alarm management focuses not only on understanding alarm behavior but utilizing that information to mitigate abnormal situations, which, if done appropriately, brings about a reduction in impact and improvement in alarm management practices.3
Practices such as ignoring noncritical alarms are commonplace within the industry because the rate at which SCADA alarms can occur, especially on larger assets, is astounding, leaving controllers unable to adequately respond to and investigate every incoming alarm.3 Alarm management applications aid in identifying such issues found in everyday practices and addressing them by acting as an integral cog in the control room management process.
By promoting compliance aspects of alarm management, modern applications can assist in not only refining alarm management, but the safety associated with well-executed control room management.
Previous Limitations
Until recently, most modern alarm management solutions have relied on databases that capture alarm information at long intervals, and that are driven by consumer-produced queries. At their core, such systems are little more than query databases. They run reports when users identify search parameters and provide only insight into what a user knows he needs to see. These designs limit consumers’ abilities to fully understand alarm activity in several ways.
As a query-driven database, such designs limit the results to only those results that fit a user’s search parameters. In other words, if a user limits his parameters when he runs a query, he also limits what information he can learn about his data. This puts the burden of searching on the user rather than the application.
The design of allowing the user to initiate and drive the data search originates in the concept of giving the user control of what he chooses to see; however, a user-driven query is neither the only nor the best method for achieving this user control. Rather, an application should provide the flexibility to allow users to interact with their data but to do so at the expense of the application, not the reverse. Likewise, by restricting data to what could be a misguided user-driven query rather than assisting the user in identifying what data he needs to see, the potential is created for overlooked information.
Query-based solutions also limit user interaction by unnecessarily delaying response time. A design that requires a user to run a query will not retrieve the appropriate data until the query is initiated, which can take up to an hour to return the requested data. This design establishes a time-consuming process for sending and receiving individual queries rather than creating a continuous experience for the user to review data on an on-going basis.
With each required query, the process restarts, as does the clock, thereby creating a cycle of new queries for re-establishing the newest data set. Moreover, this design eliminates the possibility for real-time analysis within an alarm management application.
Application Requirements
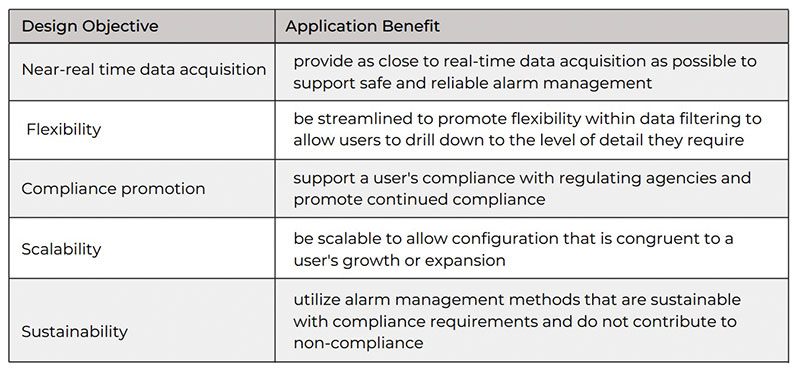
Focusing on the limitations of previous alarm management application design, NuGen Automation has defined the key design objectives that are necessary for an effective application. These aspects are lacking in many alarm management applications available on the market, and only when they are incorporated into a user-centered design can such an application be streamlined with a user’s system to provide better usability and advanced data retrieval. (Table 1)
When it comes to pipeline operations, real-time data is the pièce de résistance of data acquisition. While real-time data acquisition is possible, the financial investment for the hardware necessary to achieve real-time analysis can outweigh the return when it comes to alarm management.
By recognizing this contrast in the application market, developers must offer as close to real-time data acquisition as possible within clients’ budgets without overselling their products. Alarm management applications must evolve with the market to provide near real-time data acquisition and calculations in the form of affordable solutions to achieve highly effective alarm systems.3
Data Acquisition
Alarm management applications must provide users the flexibility to sort and filter their data by presenting them with interactive dashboards that put the control at users’ fingertips. Not all operators are created equal, and this is never as obvious as in an application configuration where each customer has his own preferences for how to view unique consoles, assets and tags.
Users must be able to sort information into relevant categories such as alarm types and drill down to more discrete levels of information. An application must also be designed in such a way that users can identify trends in the data without expert knowledge of statistical data. In other words, there must be flexibility in how a user can view data without being restricted to one dashboard for interpretation.
Without these features, applications limit their usability and thereby affect the data’s value when users must identify data sets manually.
Compliance Promotion
Compliance is a top priority for every operator, and as a regulated aspect of control room management, alarm management applications must embrace their relationship with assisting in maintaining a user’s compliance. While most products on the market strive for assisting with compliance, especially with regard to ANSI/ISA 1167-2009 Management of Alarm Systems for the Process Industries, not all applications are designed to work with changes in regulations.2
Developers of alarm management applications must promote compliance in how they present information and in how they encourage users to interact with the data, keeping in mind how their products must evolve with changes in regulations.
Operators’ needs can change, and this can include alterations to the data sources required for adequate alarm management. The old school of thought that features in consumer-driven queries neglects to consider clients’ constantly changing environments and are not designed to accommodate data sources or profiles that are added after the initial configuration.
Such additions can break the system and require developers to make the changes on the back end, often charging clients for the additional man-hours. Alarm management applications must be scalable to accommodate changes to provide clients the freedom they need to better manage their alarm databases without extra expenses or application downtime.
Scalability
Alarm management is a key aspect of control room management; therefore, any tool used to aid in such compliance must be sustainable. As regulations change and evolve, so must clients’ solutions in maintaining compliance. Alarm management applications should focus on specific qualities of compliance but not so specifically as to limit their ability to continue to serve a client as regulating agencies update existing standards and introduce new regulations.
Likewise, alarm management applications must present data in a way that allows changes to alarm management philosophies and alarm management plans to be integrated into the application with producing downtime, thereby remaining a sustainable solution for a single client over the improvement of its alarm management system.
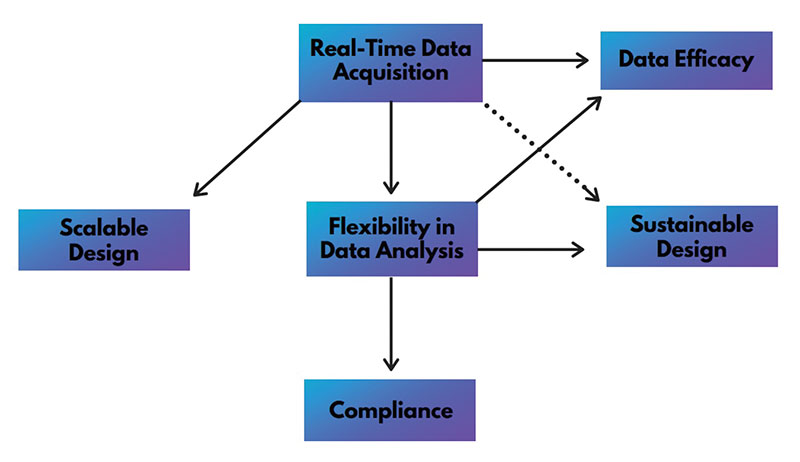
The relationship of these six application design objectives originates in the quality of data acquisition time. It is the actual or near real-time data acquisition that drives the efficiency of the application’s design as well as the competence of the data presentation. While superior graphics and visualizations can make for an impressive show of strength in data aggregation, it does little for the user if the data are limited, creating a data set that is weak and ineffectual for the user’s needs.
By anchoring the application design in real-time data acquisition, an alarm management application drives its data presentation with flexibility – providing informative data with every click that allow users to work through the data in any direction they choose.
Application Design
Recognizing the gaps that exist in today’s control room management market, NuGen Automation has designed a complete solution that assists managers with day-to-day administration and compliance-based tasks.
Our control room management suite includes five applications to support control room managers in alarm management, fatigue management, scheduling, alarm rationalization, compliance documentation and workload analysis. The NuGen Automation Alarm Management Application, one of the suite’s many modules, has energized alarm management through near real-time data acquisition with interactive and customizable dashboards that provide intuitive displays for better, faster data analysis.
By streamlining data retrieval directly through SCADA, it is possible to focus on bringing the user the most relevant data while presenting it in a customizable and easily manipulated interface that allows consumers more flexibility in their data analysis.
By pulling data continuously, our alarm management application stores search results locally for immediate filtering that allows users to drill down to alternate dashboards and comparative views with minimal wait time. By focusing on data collection for presentation as opposed to database creation for queries, it is possible to compile data into a reporting platform designed to assist users in navigating information through comparative views.
References:
1 ANSI/ISA-18.2-2016 “Management of Alarm Systems for the Process Industries.”
2 API Recommended Practice 1167, First Edition, December 2010.
3 Hollifield, Bill R. and Eddie Habibi. Alarm Management: Seven Effective
Methods for Optimum Performance. ISA, 2007.
Author: Dr. Whitney Vandiver is a compliance specialist with NuGen Automation, where she specializes in control room management compliance and assists operators with state and federal CRM audits. She previously worked for an operating company in compliance-driven documentation and holds a bachelor’s degree from the University of Central Oklahoma and an M.A. and Ph.D., both in linguistics, from Purdue University.





Comments