July 2013, Vol. 240 No. 7
Features
A Systematic Approach To Ensuring Pipeline Integrity
If oil and gas represent the lifeblood of North America’s energy, transportation and manufacturing sectors, then the oil and gas pipeline system can be considered the blood vessels. This vast and complex network, comprising thousands of lines criss-crossing the continent and spanning more than 2.6 million miles in the U.S. alone, delivers fossil fuel feedstocks to refineries, gas processors and petrochemical manufacturers, and finished fuels to end users.
This network has evolved and expanded over several decades to meet the growing energy needs of North American consumers and its increasing age is a cause for concern among pipeline owners and operators. Add to this the fact that many pipeline systems run through high-consequence areas, such as fragile ecosystems and well-populated communities, and the need for routine pipeline inspection and maintenance programs becomes more crucial than ever before.
Several high-profile pipeline accidents and environmentally damaging spills over the past several years have served to substantiate the importance of pipeline integrity management (PIM) — the means by which the appropriate people, systems and processes are put in place and properly implemented to ensure integrity throughout a pipeline’s lifecycle.
Pipeline companies rely on PIM systems to help maintain the safe and reliable operation of their pipelines, identify and analyze integrity threats, meet regulatory requirements to maintain transport licenses, and ensure that pipeline data is kept current. But as important as these systems are to a company’s environmental stewardship and profitability, each varies widely in implementation, manageability and requirements — from company to company and even from state to state.
Bureau Veritas has developed a simpler and more standardized approach to integrity management. This article reviews the steps involved in this approach as well as a methodology designed to segment sections of a pipeline based on assumed integrity threat level so as to ensure safe and reliable pipeline operations.
Back To Basics
Pipeline companies have at their disposal a host of monitoring tools, techniques and methodologies to record data and analyze pipeline systems for integrity threats, such as internal and external corrosion, accidental strikes upon the line during excavation by third parties, manufacturing or construction defects, and acts of nature such as storm damage or earthquakes. These different options can generate a substantial volume of complex data and reporting, down to a fine level of detail. But given this level of complexity, a PIM system can quickly become difficult to manage efficiently.
In addition, some PIM systems focus attention on a single problem at a specific location in the pipeline, rather than taking a more global look at the integrity of the entire system. As a result, some areas of the pipeline may not be adequately inspected or treated. This can eventually lead to pipeline ruptures that damage the company’s reputation and cost much more in repairs, cleanup and fines levied by regulatory agencies.
The Bureau Veritas PIM methodology dials back complexity in favor of a focus on fundamentals. The approach comprises six major stages. The first, company policy and strategy definition, requires the company to assess where it stands with regard to PIM, where it aspires to go and which strategy it should implement to achieve this. Within this assessment, the operator must account for local regulations and constraints, specific in-house requirements, the current age and condition of the asset and its remaining years of planned service.
The second stage, selecting a suitable methodology, asks the pipeline operator to select from (or implement per regulatory requirement) one of several management approaches, which may be risk-based, threat-based, consequence-based or take another approach. This choice is based on several factors, including the regulatory requirements in place where the pipeline is located; the condition, age and size of the system; the company’s level of in-house integrity expertise; and the ultimate goals the company wants to achieve with its program.
With these points decided, the operator then shifts to data collection and management. Creating an asset register, which is essentially a database containing all relevant pipeline data, is a critical component of this stage. The asset register should provide a complete picture of the pipeline system and deliver relevant data in the proper format for any engineer or manager requiring access.
A fundamental first question that this asset register must be able to answer is, “Where are my pipelines actually located?” While this might seem like an obvious requirement, it has not always proved to be so straightforward, given the length of pipelines, the widely different terrains through which they pass (deserts, mountain passes and under roads and waterways), and the fact that many pipelines change ownership over the course of their operating life.
In deciding which tool or set of tools to use to gather and organize pipeline data, it might be tempting to select the most current “high-tech” system. However, the most important criteria for any data management tool concerns whether it is easy to implement and use and if it has a robust and well-developed methodology.
The fifth stage of the streamlined PIM approach, study and analysis, allows the operator to develop a general methodology for the kind of inspection and maintenance that should be performed. This enables the operator to conduct an initial integrity assessment of the system which provides information and guidance on the type of ongoing assessment that will be required.
For example, the initial integrity study will highlight specific concerns in different parts of the system, which will spur the development of more specialized, expert integrity management modules (the sixth stage). These expert modules will include their own set of inspection and mitigation methodologies to ensure long-term asset integrity and compliance with regulations on a state-by-state level.
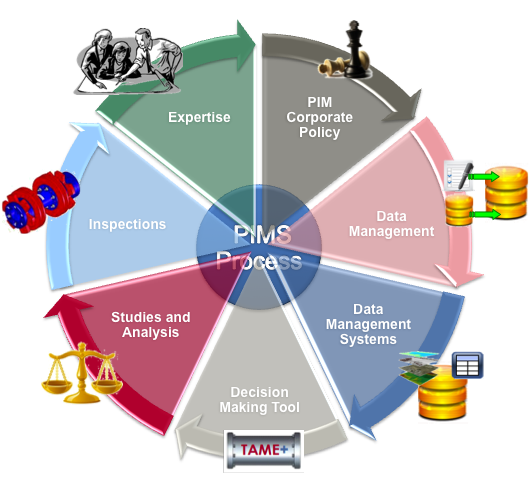
The reporting from the expert modules is then fed back into improving corporate policies and strategies, and the entire PIM process begins again with updated information. This cycle (Figure 1), which should ideally be performed on an annual basis ahead of finalizing budget plans, allows the management program to be changed as required and makes optimal use of the company’s integrity budget and resources.
Assessing Threats To Ensure Integrity
A cornerstone of the streamlined PIM system approach is a threat-based assessment known as TAME (Threats And Mitigations mEthodology), a Bureau Veritas decision-making method for modeling the threat assessment of pipelines, prioritizing corrective actions and planning inspections. This semi-quantitative model is established from industry standards such as API 1160 for liquid pipelines and ASME B31.8S for gas pipelines, and incorporates integrity best practices provided by the field experiences of subject matter experts. Because pipeline integrity is a concern for operators of both smaller and larger pipeline networks, the method is applicable to all pipeline operators in any region or state.
Figure 2: An example of the steps in the Bureau Veritas TAME process in which potential threats are identified (box at left) and then grouped and prioritized such that an integrity management policy can be developed (box at right).
The methodology begins with the formation of an integrity implementation team, which includes both experienced engineers with first-hand knowledge of integrity threats and less experienced engineers who provide a fresh perspective on new potential threats. This team, comprising both pipeline company and Bureau Veritas personnel and led by a chairperson and facilitator, holds a brainstorming session to identify all potential integrity threats and their location in the system (Figure 2).
These threats are then categorized and prioritized, with higher-risk threats receiving greater priority, in a threats tree (Figure 3). This tree provides a hierarchy of threats for different segments of the pipeline system. Each segment, which can be considered a branch on the tree, will include a list of integrity threats that are specific to that segment.
These threats are numerically weighted based on the severity of their impact on the segment. For example, in a segment reserved for external corrosion, an exterior polyethylene coating would be weighted as a low integrity threat, because it is designed to protect the pipeline from corrosive attack. Conversely, an uncoated pipe would have a much higher threat risk value.
Figure 3: An example of a Bureau Veritas threats tree developed in a simple spreadsheet format.
With this information, coupled with proposed mitigation solutions for each threat, an algorithm is developed to calculate the financial, safety and environmental impact of each threat. Finally, an integrity policy is defined, which prioritizes mitigation activities and inspection planning based on the threats.
This methodology has been automated in a user-friendly data collection and planning software system known as TAME+. The software allows for dynamic segmentation of small pipeline networks (less than 500 km in length) and up to 15 pipelines at a time. The system consists of several information tabs that together provide a comprehensive plan of action for assuring integrity of different segments, and of the pipeline as a whole (Figure 4).

Figure 4: A representative home screen, or dashboard, highlighting the main components of the Bureau Veritas TAME+ system.
In the information tab, the integrity team inputs definitions of different threat categories, as well as the weight of each threat and calculation rules. Comments describing the threat or any other relevant information can also be included here. Under the data and scores tab, the team can input threat attributes and their weighted score from the information tab, launch dynamic segmentation, run calculations to determine the likelihood that a threat will cause an integrity issue and report the expected consequences as a numerical score.
The likelihood and consequence data can be viewed in a risk matrix format under the matrix tab. In the charts tab, the team can review, in a pie-chart format, how the threats are distributed for a given category, and check the quality of the data input.
Under the mitigations tab, the team can define, add or activate specific mitigations for a given threat, which the system uses to calculate a new weighted threat score based on implementing a given mitigation strategy. The user can then add these mitigation measures into their system, and manage their inspection schedules — by both frequency and type — under the inspections tab.
The major outputs of the TAME+ system include the segmentation of the pipeline, the calculated integrity risk for each segment and the inspection method and frequency — all of which can be exported to a spreadsheet format. These outputs form the basis of the pipeline operator’s inspection and mitigation program, which can be updated to reflect changing operating parameters, new integrity risks and regulatory requirements.
While proper pipeline integrity management is vital to every operator’s profitability and regulatory compliance, it need not be overly complicated. The systematic and streamlined PIM approach can help operators achieve environmental compliance and make the best use of their integrity management budget, regardless of their pipeline system’s location, age or size.
Author:

Karine Kutrowski is the manager of the Design Review and Integrity Management Department for Bureau Veritas. With nearly a decade of experience in pipeline integrity management in the oil and gas industry, she holds a bachelor’s of science degree in power generation from the University of Groningen, The Netherlands, and a master’s of industrial systems degree with specialty in safety and reliability from the University of Technology of Troyes, France.





Comments